How to Retrieve Hardware and Software Information From the Network Devices
What is Networking Hardware?
Networking hardware includes all computers, peripherals, interface cards and other equipment needed to perform information-processing and communications within the network. CLICK on the terms below to learn more virtually those pieces of networking hardware.
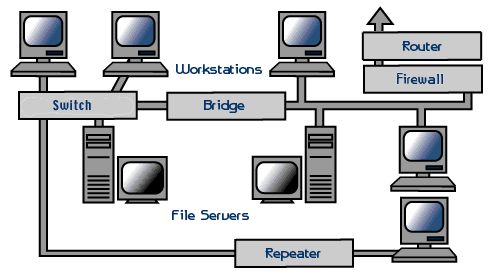
- Workstations
- Hubs
- Bridges
- Firewalls
- Routers
- FileServers
- Repeaters
This section provides information on the following components:
- Network Servers
- Workstations
- Network Interface Cards
- Switches
- Repeaters
- Bridges
- Routers
- Firewalls
File/Network Servers
One or more than network servers is a part of almost every local surface area network.These are very fast computers with a large amount of RAM and storage infinite, forth with a one or more fast network interface card(s). The network operating organization provides tools to share server resources and data with network users. A sophisticated permissions-treatment arrangement is included, and so that access to sensitive data can be advisedly tailored to the needs of the users. For small networks, a singe network server may provide access control, file sharing, printer sharing, email, database, and other services.
The network server may be responding to requests from many network users simultaneously. For instance, information technology may exist asked to load a word processor program to 1 workstation, receive a database file from another workstation, and store an e-mail bulletin during the same time period. This requires a estimator that can store and chop-chop share large amounts of information. When configuring such a server, upkeep is normally the decision-making cistron. The post-obit guidelines should be followed:
- Fastest processor(s)
- Big amount of RAM
- multiple large, fast hard drives
- Extra expansion slots
- Fast network interface card(s)
Optionally (if no other such devices are available on the network):
- A RAID (Redundant Array of Inexpensive Disks) to preserve large amounts of data(fifty-fifty later on a deejay failure)
- A redundancy unit (i.e. DAT tape bulldoze, removable hard drives, or CD/DVD/BluRay burner)
Workstations
Computers that humans use are broadly categorized as workstations. A typical workstation is a reckoner that is configured with a network interface card, networking software, and the appropriate cables. Workstations exercise not necessarily demand large storage difficult drives, considering files can exist saved on the file server. Nearly any figurer tin serve as a network workstation.
Laptops/Mobile Devices
Laptops and other mobile devices are becoming more and more than mutual. These devices typically have pocket-size internal storage, but enough ability to serve every bit a workstation for users on the go. These machines nearly e'er have a wireless adapter to allow quick network connections without cumbersome cabling. In a schoolhouse surroundings with good wireless coverage, a mobile device user can motion about the campus freely, and remain continuously connected to the network.
Network Interface Cards
The network interface card (NIC) provides the concrete connection between the network and the computer workstation. Most NICs are internal, and they are included in the purchase of most computers. Network interface cards are a major factor in determining the speed and performance of a network. It is a skilful idea to use the fastest network card available for the type of workstation you are using.
The most mutual network interface connections are Ethernet cards and wireless adapters.
Ethernet Cards
Ethernet cards are usually included with a computer, although additional ethernet cards can be purchased and installed on nearly computers,. Ethernet cards can incorporate connections for either coaxial or twisted pair cables (or both) (See fig. 1). If it is designed for coaxial cable, the connexion will exist BNC. If it is designed for twisted pair, it will have a RJ-45 connection. Some Ethernet cards also contain an AUI connector. This tin be used to adhere coaxial, twisted pair, or fiber eyes cablevision to an Ethernet card. When this method is used there is ever an external transceiver attached to the workstation. Only the RJ-45 connector is found on well-nigh mod ethernet cards (Encounter the Cabling section for more information on connectors.)
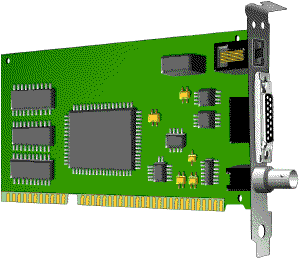
Fig. i. Ethernet card.
From height to bottom:
RJ-45, AUI, and BNC connectors
Wireless Adapters
Wireless adapters are establish in most portable devices, such as laptops, smart phones, and tablet devices. External wireless adapters can be purchased and installed on nigh computers having an open USB (Universal Serial Bus) port, or unused expansion slot. (See the Cabling department for more information on connectors.)
Switches
An ethernet switch is a device that provides a central connexion betoken for cables from workstations, servers, and peripherals. In a star topology, twisted-pair wire is run from each workstation to a key switch/hub. Well-nigh switches are active, that is they electrically amplify the indicate as it moves from 1 device to another. The predecessor of the switch was the hub, which broadcasted all inbound packets out all ports of the device, creating huge amounts of unnecessary network traffic. Modern switches build a port map of all IP accost which respond on each port, and just broadcasts on all ports when it doesn't take a packet'southward target IP address already in its port map. Switches are:
- Usually configured with 8, 12, or 24 RJ-45 ports
- Often used in a star or tree topology
- Bachelor as "managed" or "unmanaged", with the later less expensive, but adequate for smaller networks
- direct replacements for hubs, immediately reducing network traffic in most networks
- Usually installed in a standardized metallic rack that besides may shop network servers, bridges, or routers
Repeaters
Since a bespeak loses strength as it passes along a cablevision, it is frequently necessary to boost the indicate with a device called a repeater. The repeater electrically amplifies the signal information technology receives and rebroadcasts information technology. Repeaters tin be carve up devices or they tin be incorporated into a concentrator. They are used when the full length of your network cable exceeds the standards set for the type of cable existence used.
A skillful example of the employ of repeaters would exist in a local area network using a star topology with unshielded twisted-pair cabling. The length limit for unshielded twisted-pair cablevision is 100 meters. The about common configuration is for each workstation to be connected past twisted-pair cable to a multi-port agile concentrator. The concentrator amplifies all the signals that laissez passer through information technology allowing for the total length of cable on the network to exceed the 100 meter limit.
Bridges
A bridge is a device that allows you to segment a large network into two smaller, more efficient networks. If you lot are calculation to an older wiring scheme and want the new network to be up-to-appointment, a bridge can connect the two.
A bridge monitors the data traffic on both sides of the network so that it can pass packets of data to the correct location. Most bridges can "listen" to the network and automatically effigy out the address of each figurer on both sides of the span. The bridge can inspect each message and, if necessary, broadcast it on the other side of the network.
The bridge manages the traffic to maintain optimum operation on both sides of the network. You lot might say that the span is like a traffic cop at a busy intersection during rush 60 minutes. It keeps information flowing on both sides of the network, but it does not allow unnecessary traffic through. Bridges tin can be used to connect dissimilar types of cabling, or concrete topologies. They must, however, be used between networks with the same protocol.
Routers
Routers are the traffic directors of the global internet. All routers maintain circuitous routing tables which allow them to determine appropriate paths for packets destined for whatever address. Routers communicate with each other, and forward network packets out of or into a network. Here's an example:
Y'all desire to search for something on the cyberspace using a search engine. You open a browser on your workstation. The browser opens to a bare page (not usually the default, but appropriate for this example). You type "http://www.google.com" into the URL (Universal Resource Locator) address line of the browser. The browser software packages up the URL you typed, and sends it with a request for an IP address to the DNS (Domain Name Server) that has been set up in your network adapter'southward configuration. The domain server returns an IP, such equally 74.125.67.103 (actual address returned past DNS for google.com on June 7th, 2011). The browser ships the asking for that IP address off to the network card, which bundles the request into an ethernet parcel, destined for 74.125.67.103. The network card sends the package to the gateway of your network, which opens the header of the package, and makes a conclusion that the packet is traveling out of your network, in search of 74.125.67.103. Your network's router has routing tables which it has been building from communicating with other routers, and potentially augmented with "static routes", which are specific paths added by your network's administrators to brand the task of accessing sure networks easier, or faster, or in some cases, not possible. In this case, I notice that my router knows about another router at my ISP(Internet Service Provider), which in turn has several more routers that are all on networks of which I am only a pocket-sized node, much like finding an atom of a molecule of a piece of grit on a stone on a moon of a planet of a sunday of a galaxy of the universe. In whatever case, the parcel gets passed from router to router, each time moving out of the subnets of the packet sender, towards a router that will know where the desired server is. The packet finally reaches the router of the network at 74.125.67.103, which dutifully delivers the packet to the server at that IP accost. The server carefully crafts a response, and sends a reply back, which follows the same process to go the response "Yes. Go ahead" dorsum to the requester. Whew. And that's just the initial asking.
While bridges know the addresses of all computers on each side of the network, routers know the addresses other routers which in turn know about their own networks. Routers can even "heed" to entire networks to determine which sections are busiest -- they can and so redirect data around those sections until traffic congestion clears.
So, routers are network gateways. They move network packets from one network to another, and many can convert from 1 network protocol to another as necessary. Routers select the best path to route a bulletin, based on the destination address of the packet. The router tin direct traffic to prevent head-on collisions, and is smart plenty to know when to direct traffic forth back roads and shortcuts.
If you have a school LAN that you want to connect to the Net, you will demand to purchase a router. In this example, the router serves as the forwarder betwixt the information on your LAN and the Internet. It besides determines the best route to send the data over the Cyberspace.
Firewalls
A firewall is a networking device that is installed at the entrance to a LAN when connecting a networks together, particularly when connecting a private network to a public network, such as the internet. The firewall uses rules to filter traffic into and out of the individual network, to protect the private network users and data from malevolent hackers.
Firewalls are either hardware or software, depending on their intended utilise. A firewall used to protect a network is a hardware device that should exist installed in the network betwixt the router and the network. Most all hardware firewalls will have at least two ports, labeled "Trusted" and "Untrusted". These terms imply the truthful nature of the firewall's responsibility to the individual network. The public network is connected to the untrusted network port, and the private network is connected to the trusted port.
Firewall rules are commonly simple, consisting of a verb, either allow or deny, the management of the traffic, either inbound or outbound, and an accost or other network traffic identifier. Firewall rules are cumulative, so general rules may exist specified, and exceptions added as necessary. Some examples are:
- Allow outbound all (all private network users tin practise anything on the public network)
- Deny entering all (default setting to forestall all traffic from the public or untrusted port, to the private port)
- Allow inbound port 80 (allow internet web traffic to come into network to find web servers)
- Permit inbound port 80 destined to 170.200.201.25 (permit entering web traffic to a specific spider web server on your private network)
- Deny entering from 201.202.1.1/24 (deny all inbound traffic from a specific IP address or range of addresses)
Software firewalls are normally included in mod workstation and server operating systems. They operate in a similar way equally hardware firewalls, except that they filter traffic in and out of the automobile itself. These software firewalls are typically unnoticed by machine users, and only demand attention occasionslly when an internet-connected awarding don't piece of work equally expected. The software firewall should e'er exist considered a "suspect" in such cases. The problem is easily resolved, by setting an exception rule in the firewall for the software that is attempting to communicate.
0 Response to "How to Retrieve Hardware and Software Information From the Network Devices"
Post a Comment